Security at the Cyber-Physical Intersections
In my previous post Complexity impedes Security I covered the simplification principles. The Cyber-Physical interactions are the focus in this post.
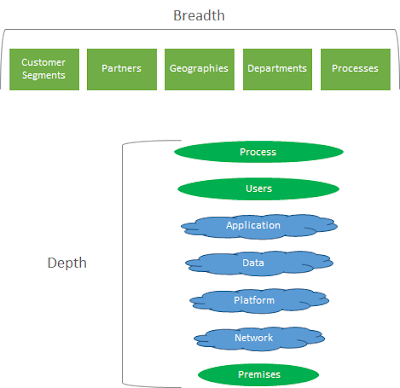
- The Physical-space comprises the geographical locations and the users and the tools in them orchestrated within a business process context.
- The Cyber-space comprises the Network that provides the connectivity, the Platforms that provide containers for the Applications to run on hence process the Data.
- Enterprises operate their businesses across the breadth and depth of their capabilities using internal and external entities that share each others’ physical and cyber space.
- Today’s Enterprises, old and new alike, operate a network of processes that transact across physical and cyber boundaries. I present a viewpoint that Security vulnerabilities are the highest in these intersections.
A holistic Security should consider two important factors
- Adequate security validations at all Cyber-Physical divides
- Address Security with an end-to-end process in context
The network becomes the glue between the Cyber and Physical entities, however, there may be various networks at play as the process steps are carried out end-to-end.
Automating the end-to-end process seamlessly is one of the necessary simplification principles that significantly improves Security.
The tools today are inadequate in addressing the cyber-physical divide and this chasm is filled with security risks. A paradigm shift is required through adoption of Digital Transformation methods such as blockchain.





Comments
Post a Comment
What do you think?