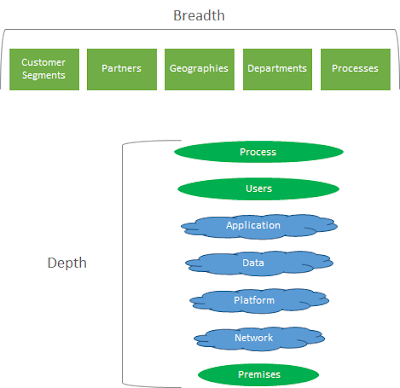
A well-thought-out idea, a powerful marketing message, an informative info-graphic, a restaurant menu card, a movie poster, a cheat sheet, London tube map. What is common in all of the above? The title of this post is a hint. They are all something on a page. Anything that fits a page is a well articulated viewpoint of a customer. Anything on a page is an amazing vehicle to reach the information to the right audience at the right place and time. Three principles to bear in mind: 1. Focus on the outcome of the process (why) 2. Take the viewpoint of the audience (who, when, where) 3. Apply sophistication to the tools yet keep the output simple (how)